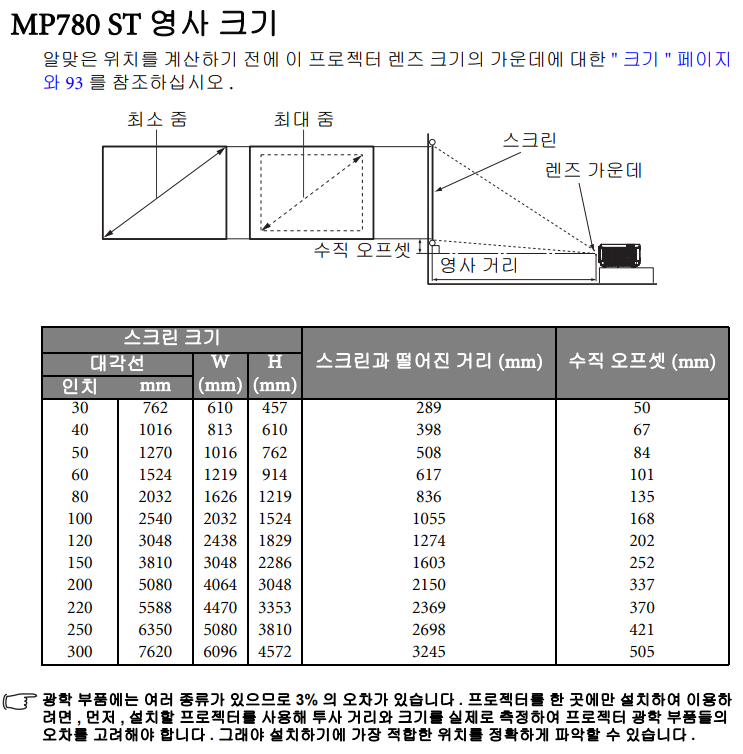
당근으로 8만원에 후딱 업어옴
박스 제외하면 거의 풀박스! 조금 지저분 했지만 물티슈로 닦으니 새거 같아졌다.

pw700 19V 3.42A 대충 65W 정도로 이전의 벤큐 250W에 비하면 천사 ㅋㅋ

어제 아버지가 안쓰시는 삼각대 하나 뽀려서 오늘 장착!

중간절전이지만 형광등 켜도 이정도 까지 나온다. 역시 550 안시 보단 700을 한건 최선의 선택이었나?!

스크린 쉐어를 지원하는데 특이하게(?) 와이파이 설정은 없고..
스크린 쉐어하면 S10 FHD를 스케일링 하면서 해상도가 개판이 된다.
그런데 "연결된 기기에서 전체 화면"을 누르면 출력 장치의 해상도를 따르면서 깨끗하게 나온다.

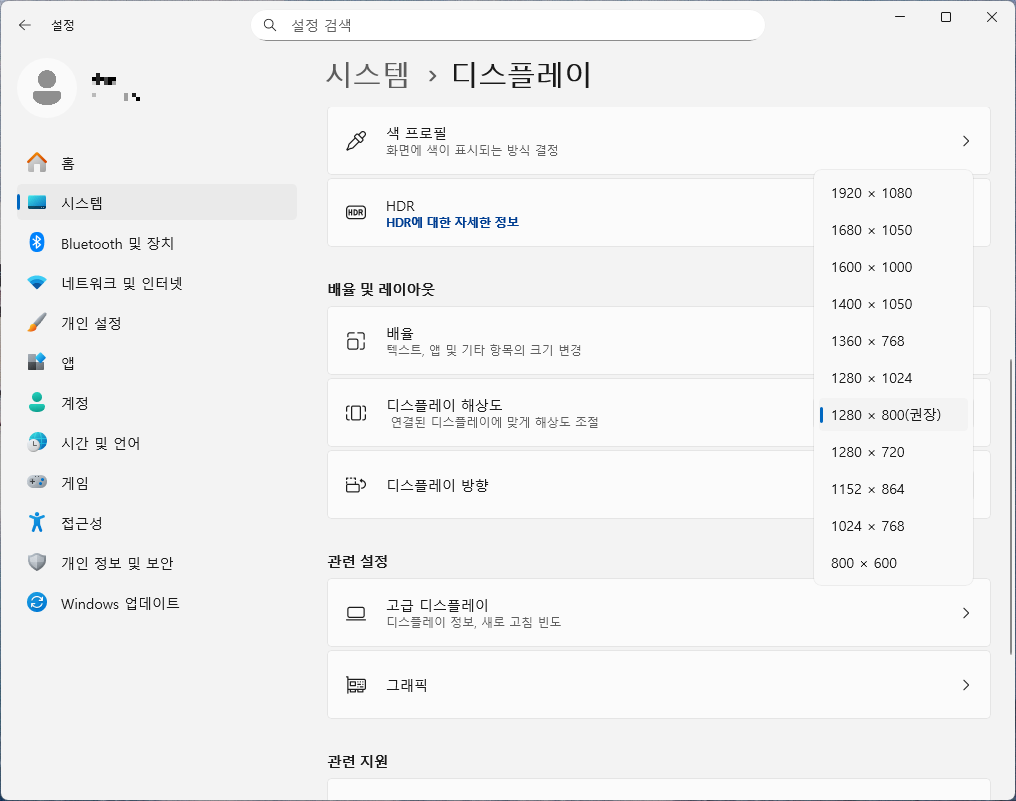
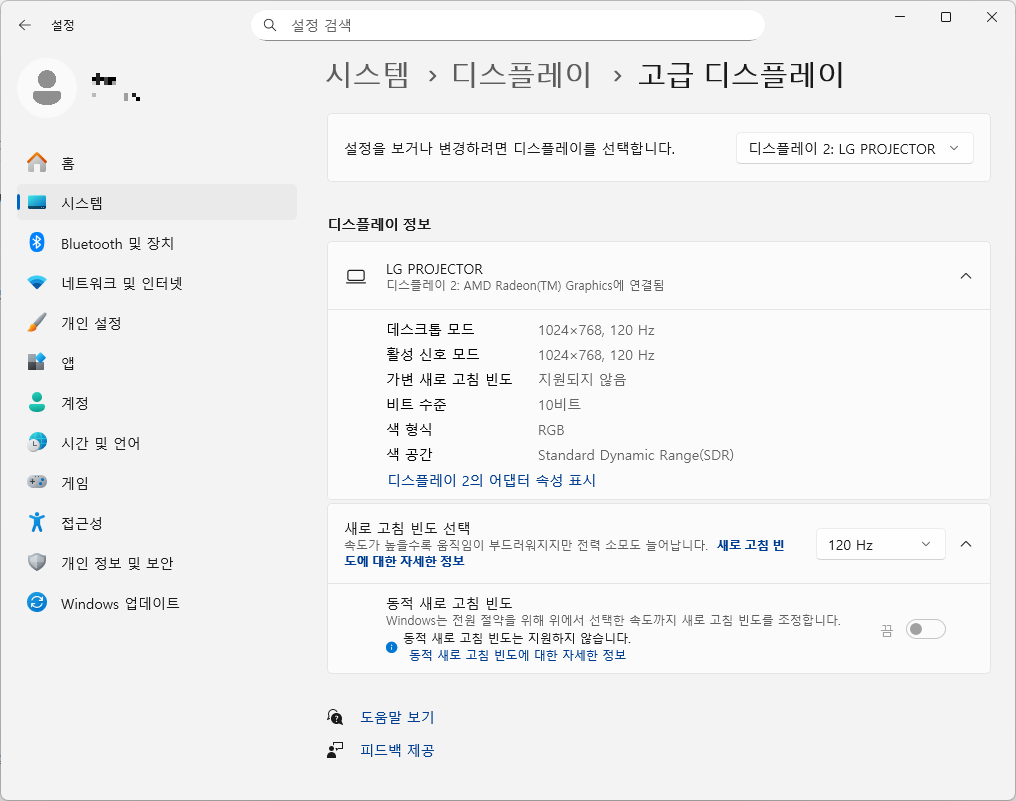
1280x800 을 추천 해상도로 띄우긴 하지만, 120hz로 고르는 순간 1024x768로 고정된다.
개인적으론 1280x720은 작업용으로는 무리지만 1280x800은 아쉬운대로 쓸 수 있어서
해상도 차이는 구매를 고려했던 ph550에 비하면 조금 고민하게 했던 부분.
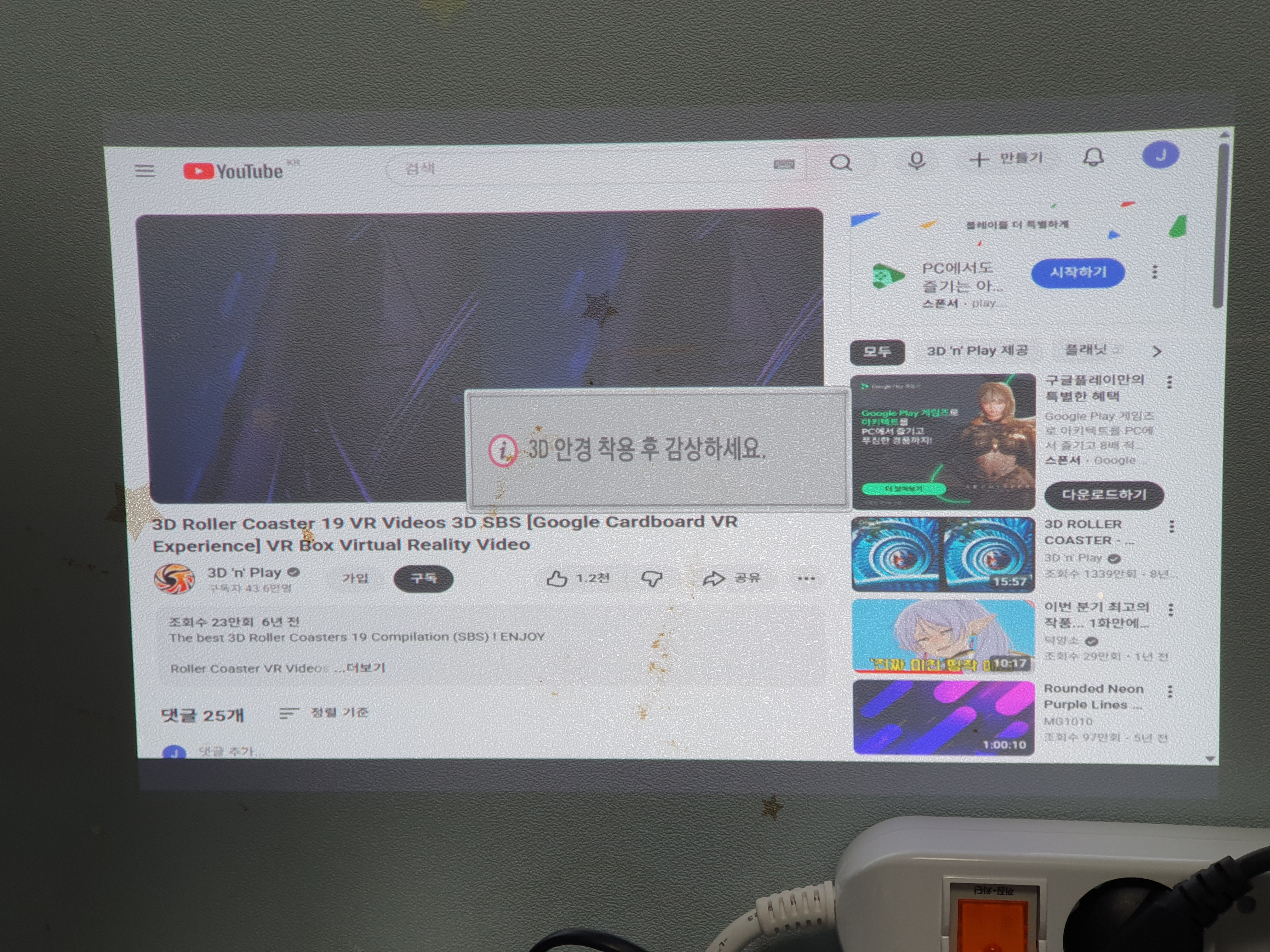
리모컨을 누르거나, 메뉴에서 들어가서 켜면 되는데
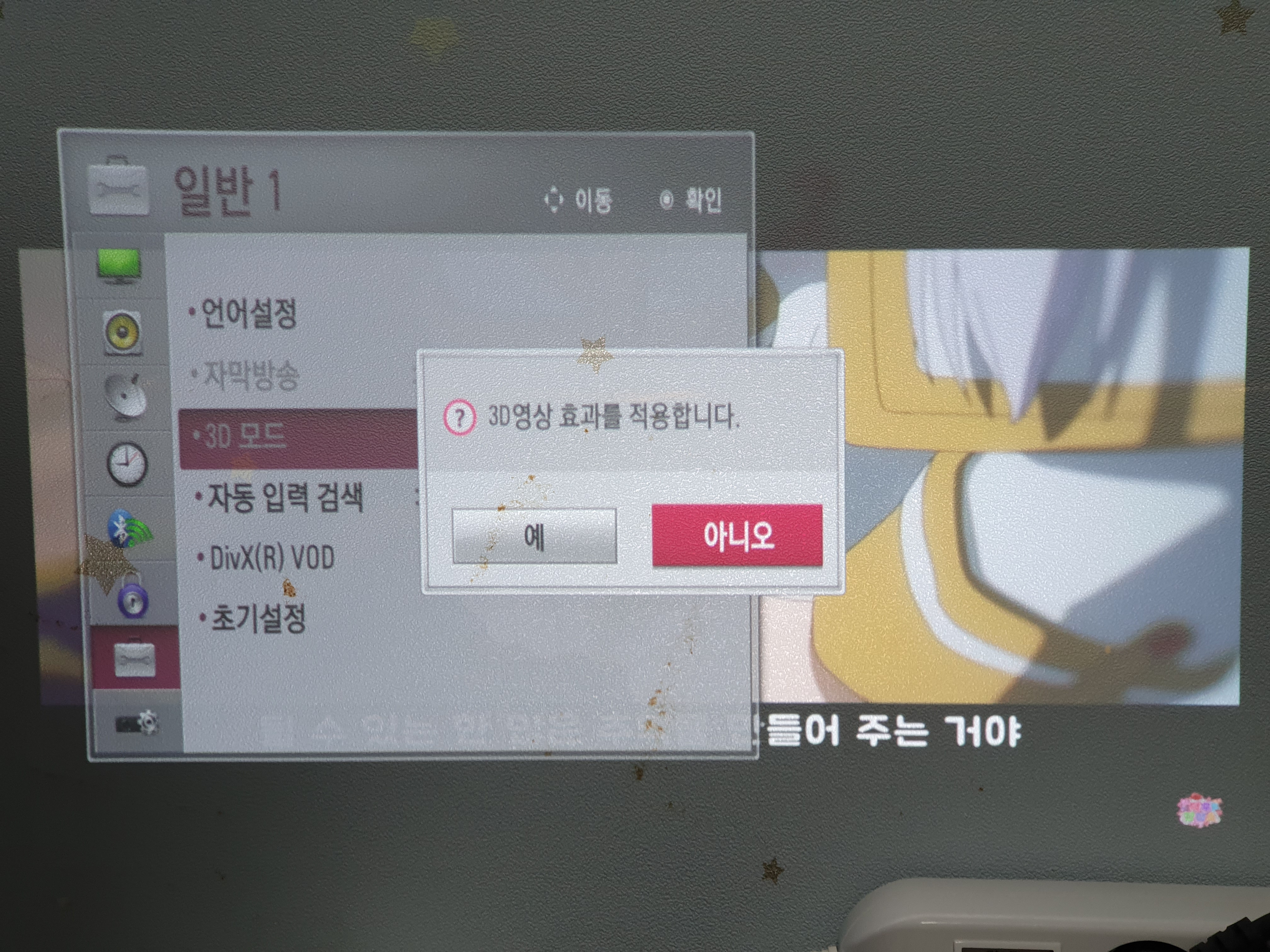
솔찍히 눈으로 봐서는 티가 안난다.
LG TV의 3D처럼 side by side 나 top and bottom 같은 설정도 없고 바로 모드가 변경된다.
'하드웨어 > Display 장비' 카테고리의 다른 글
| pw700 edid 덤프 (0) | 2025.10.27 |
|---|---|
| lg pw700 3d 모드 활성화 super slow 촬영 (0) | 2025.10.26 |
| benq mp780st 마운트 (0) | 2025.10.19 |
| 스마트빔 실버 IC200T (0) | 2025.09.29 |
| 3d dlp 120Hz가 왜 망했냐면.. (0) | 2023.08.27 |